Log4j, all the news

Hackers have launched more than 1.8 million attack attempts through the Log4J vulnerability. During the week, the second Log4j vulnerability was discovered with a patch already released
A huge flaw in open source is putting millions of systems at risk: we are talking about the Log4j vulnerability.
Experts say the bug leaves hundreds of millions of systems vulnerable to cyber attacks. ( Here is Startmag 's insight into Log4j, here is the new cyber threat ).
The exploits began on December 1, according to Cloudflare, and an initial alert from Cert New Zealand triggered more from Cisa, the U.S. cybersecurity agency and the United States' National Cyber Security Center. United. On 9 December in Italy the National Cybersecurity Agency thought about sounding the alarm of "a vast and diversified attack surface on the entire network", defining the situation as "particularly serious".
Log4j is used in many forms of enterprise and open source software, including cloud platforms, web applications, and email services. This means that there is a wide range of software that could be at risk from attempts to exploit the vulnerability.
As Axios points out, “the key now is to identify and repair all systems at risk. Complicating the task is the fact that many governments, companies and consumers probably don't know if they have products that use the code. "
Yesterday, cybersecurity firm Check Point said it detected over 1.8 million attempts to exploit the bug this week. Over 46% come from known harmful groups.
But it doesn't stop there. According to the Zdnet website, security experts on Tuesday identified a second vulnerability involving Apache Log4j.
All the details.
WHAT IS LOG4J
Log4J is an open source library included in a range of software, services and hardware, such as network devices from companies such as Amazon, Broadcom, and Cisco.
Like many pieces of open source code, thanks to its extensive license, developers frequently use Log4J, Sean Gallagher, senior threat researcher at Sophos, told Axios .
THE FOUL IN LOG4J DISCOVERED BY ALIBABA
Late last month, a security researcher at the Chinese IT firm Alibaba Cloud discovered the flaw in the Log4j code. The latter reported the problem to the Apache Software Foundation, the American non-profit organization that oversees hundreds of open source projects including Log4j, to give it time to fix the problem before it was publicly revealed. This kicked off a rush to close the vulnerability, and a patch was released earlier this month.
ATTACK VULNERABLE SYSTEMS
The Log4J flaw allows attackers to easily gain remote control over computers running apps in Java, a popular programming language.
According to Gallagher, this could include commands to download and install all kinds of code on vulnerable systems, including cryptocurrency miners or other malicious software.
“Organizations often have no idea these libraries are part of their applications, especially if developed by third parties who may or may not support them after implementation,” Gallagher said.
ALL ATTACKS CONDUCTED SO FAR
Since last Friday, the Check Point cybersecurity group has revealed at least 1.8 million attack attempts via the Log4j bug. The company added that in some places its researchers found more than 100 attacks per minute.
WHAT CISA HAS DECLARED
In the United States, CISA said it was adding the vulnerability to the list of mandatory vulnerabilities for federal agencies to correct.
DISCOVERING A SECOND VULNERABILITY
Meanwhile, researchers identified a second flaw in Log4j on Tuesday, according to the Zdnet website.
The description of the new vulnerability, CVE 2021-45046, states that the fix for the address CVE-2021-44228 in Apache Log4j 2.15.0 was "incomplete in some non-default configurations".
Thankfully, Apache has already released a patch.
WHAT MICROSOFT HAS DISCOVERED
Microsoft said Tuesday that it found evidence of the defect used by monitored groups based in China, Iran, North Korea and Turkey. These include an Iran-based ransomware group, as well as other groups known to sell access to systems for the purpose of ransomware attacks. Such activities could lead to an increase in ransomware attacks along the way, the Redmond giant said.
That is the ramsomware-type attacks that in recent months have hit the Lazio Region , Siae, but also Mediaworld and the San Carlo company.
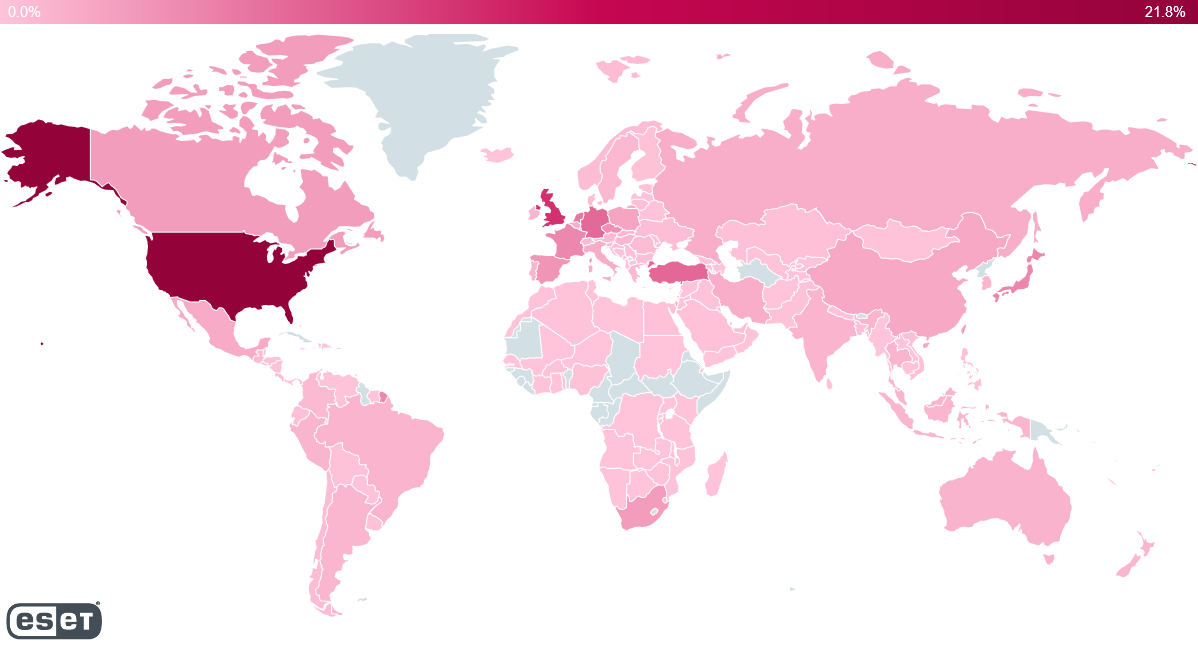
THE MAP OF THE MOST AFFECTED STATES
Finally, the international security company Eset released a map showing where the attempts to exploit Log4j took place, taken from the Zdnet site. As can be seen, the highest volume occurred in the United States, the United Kingdom, Turkey, Germany and the Netherlands.
“The sheer volume of our findings confirms that this is a large-scale problem that will not go away anytime soon,” said Roman Kováč, Eset's Chief Research Officer.
This is a machine translation from Italian language of a post published on Start Magazine at the URL https://www.startmag.it/innovazione/log4j-tutte-le-novita/ on Thu, 16 Dec 2021 10:47:56 +0000.
